
Understanding Ransomware
Ransomware is a type of malicious software (malware) that encrypts a victim’s files or locks them out of their system, making the data inaccessible until a ransom is paid. The attacker typically demands payment in cryptocurrency, such as Bitcoin, to ensure anonymity. Ransomware can spread through phishing emails, malicious downloads, or exploiting vulnerabilities in software and networks. This form of cyber attack can have devastating effects on businesses, leading to significant financial loss, operational disruption, and damage to reputation. Ransomware attackers often demand payment in cryptocurrency to avoid detection, making it difficult to trace and recover the funds. The rapid evolution of ransomware techniques poses an ever-growing threat, making it essential for
businesses, especially small and medium-sized enterprises (SMBs), to stay informed and prepared to combat these attacks effectively.

Being Prepared
For SMBs, the impact of a ransomware attack can be particularly severe due to limited resources and potentially less robust security measures compared to larger enterprises. Preparedness is critical to mitigating the risks associated with ransomware. This includes implementing comprehensive cybersecurity strategies, regular employee training, and maintaining up-to-date backups. Being prepared not only helps in preventing attacks but also ensures a swift and effective response in the event of an incident. By understanding the nature of ransomware and adopting proactive measures, SMBs can protect their operations, secure sensitive data, and maintain customer trust, ultimately safeguarding and reducing the risk from future security incidents.

How Ransomware Attacks Occur
Ransomware attacks often begin with a phishing email that contains a malicious attachment or a link to a compromised website. When the victim opens the attachment or clicks the link, the ransomware is downloaded and executed on their system. Once activated, the ransomware encrypts files on the infected system and sometimes spreads to other connected devices and networks. The victim is then presented with a ransom note, demanding payment to decrypt the files or regain access to their system. Ransomware attacks often begin with a phishing email that contains a malicious attachment or a link to a compromised website. When the victim opens the attachment or clicks the link, the ransomware is downloaded and executed on their system. Once activated, the ransomware encrypts files on the infected system and sometimes spreads to other connected devices and networks. The victim is then presented with a ransom note, demanding payment to decrypt the files or regain access to their system.
Common Types of Ransomware
Ransomware attacks often begin with a phishing email that contains a malicious attachment or a link to a compromised website. When the victim opens the attachment or clicks the link, the ransomware is downloaded and executed on their system. Once activated, the ransomware encrypts files on the infected system and sometimes spreads to other connected devices and networks. The victim is then presented with a ransom note, demanding payment to decrypt the files or regain access to their system. Ransomware attacks often begin with a phishing email that contains a malicious attachment or a link to a compromised website. When the victim opens the attachment or clicks the link, the ransomware is downloaded and executed on their system. Once activated, the ransomware encrypts files on the infected system and sometimes spreads to other connected devices and networks. The victim is then presented with a ransom note, demanding payment to decrypt the files or regain access to their system.

Crypto Ransomware
This type encrypts files on a victim’s system, making them inaccessible. The attacker then demands a ransom for the decryption key. Examples include CryptoLocker and WannaCry.

Locker Ransomware
Instead of encrypting files, locker ransomware locks the victim out of their system, preventing access to applications and data. The attacker demands a ransom to unlock the system. Examples include WinLocker and Reveton.

Scareware
This type of ransomware pretends to be legitimate software or security alert, claiming that the victim’s system is infected with malware. The attacker demands payment to ‘remove’ the fake threat. Examples include FakeAV and Rogue.

RaaS (Ransomware as a Service)
This model involves ransomware developers providing their malicious software to affiliates, who then distribute the ransomware and share the profits with the developers. Examples include GandCrab and DarkSide.
How Ransomware Spreads
Ransomware spreads through several common methods, each designed to exploit vulnerabilities in human behavior or computer systems.
One prevalent method is phishing emails, where cybercriminals send deceptive messages that appear to be from trusted sources. These emails often contain malicious attachments or links that, when opened, download ransomware onto the victim’s device. Another common vector is malicious websites. These sites, either designed by attackers or compromised legitimate sites, host malicious code that can automatically download ransomware when visited. Users can inadvertently access these sites through misleading ads or links. Additionally, exploit kits are automated tools used by attackers to scan for and exploit known vulnerabilities in software and systems. Once a vulnerability is found, the exploit kit delivers the ransomware payload.
Regular software updates, user education, and robust security measures can help protect against these methods of ransomware spreading.
Ransomware Spreads by these 3 common methods.
Understanding the Financial and Legal Impact from a Data Breach
Around 40% of all cyber breaches impact businesses with fewer than 100 employees.
Data breaches can lead to significant regulatory fines and customer lawsuits, posing severe financial and legal challenges for small and medium-sized businesses (SMBs). Recent examples illustrate these consequences vividly. In 2023, Bosley Inc., a hair restoration company, settled for $500,000 following a 2020 data breach that compromised customer information due to inadequate cybersecurity measures. Plaintiffs claimed that Bosley failed to protect their data and delayed informing customers about the breach, resulting in risks of fraud and identity theft. Customers had to invest time and resources to safeguard themselves, highlighting the importance of timely and effective breach management.
Similarly, Herff Jones, a graduation product manufacturer, faced a $4.35 million settlement in January 2023 after a data breach exposed customer payment card information in mid-2022. The class action lawsuit against Herff Jones argued that the company neglected reasonable data protection measures, leading to the breach. Although the company did not admit to any wrongdoing, it agreed to the substantial settlement to resolve the lawsuit, emphasizing the costly repercussions of data protection failures.
Accellion and San Juan Regional Medical Center also encountered significant settlements due to data breaches. Accellion settled for $8.1 million in early 2024 for a breach that affected millions in 2020, attributed to insufficient security measures. San Juan Regional Medical Center in New Mexico faced a class action lawsuit after a 2020 breach exposed nearly 69,000 patients’ private information. The settlement included two years of complimentary credit monitoring and identity theft protection services, with additional compensation for affected individuals.
Most cybersecurity incidents at SMBs cost between $826 and $653,587.
Cyber Insurance
What is Cyber Insurance

Cyber Insurance policies provide SMBs with financial support and resources to respond to and recover from cybersecurity incidents such as data breaches, ransomware attacks, and other cyber threats. The average cost of cyber insurance for small to medium-sized businesses typically ranges from $1,000 to $7,500 per year, depending on factors such as business size, industry, and level of coverage needed (BizTech Magazine, AdvisorSmith). These policies can cover various expenses including legal fees, customer notification, crisis management, and data recovery. Due to the rising frequency and severity of cyber attacks, premiums have increased, with some SMBs paying significantly higher rates depending on their risk profile and security posture (Founder Shield, Bitdefender).
Several well-known companies offer cyber insurance for SMBs. Chubb is recognized for comprehensive coverage options and a strong emphasis on risk management services. Hiscox offers tailored policies specifically designed for small businesses, including cyber liability insurance. Travelers provides a range of cyber insurance products with options for incident response services and coverage for business interruption. Beazley specializes in cyber liability and data breach insurance, offering robust policies with extensive support services. AXA XL focuses on large and small businesses with customizable cyber insurance policies and a focus on risk prevention and management. These companies are known for their comprehensive coverage and support services, making them suitable choices for SMBs looking to mitigate the financial impact of cyber incidents and enhance their cybersecurity posture.
Factors to Consider when Purchasing
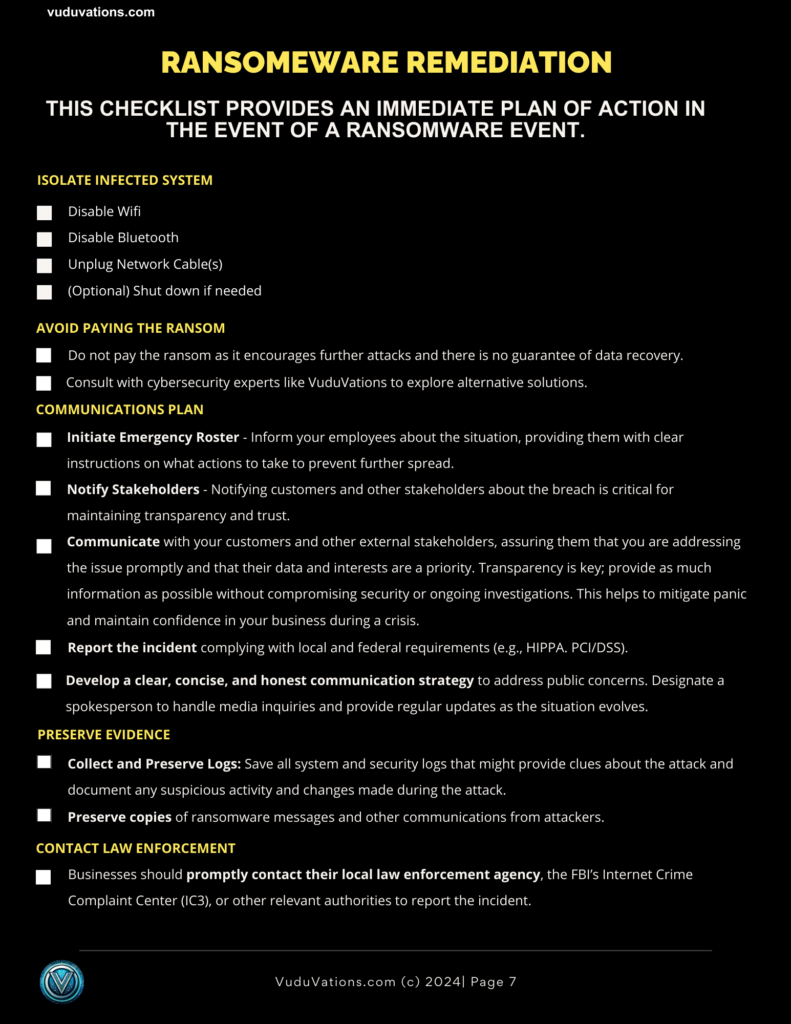
Ransomware Remediation Checklist
The Aftermath
Conducting the Post-Mortem Analysis
Conducting a post-mortem analysis after a ransomware attack is crucial for understanding the incident and preventing future occurrences. This process involves a thorough examination of how the attack was carried out, identifying the vulnerabilities that were exploited, and assessing the effectiveness of the response measures taken. By analyzing logs, reviewing security alerts, and interviewing affected personnel, businesses can pinpoint weaknesses in their systems and processes. This detailed analysis provides valuable insights that inform the development of stronger defenses and helps in creating a more resilient cybersecurity strategy. Additionally, documenting the findings and lessons learned during the post-mortem analysis is essential for improving incident response plans and ensuring the organization is better prepared for future threats.

Improving Security Measures
Implementing enhanced security measures based on lessons learned from a ransomware attack is a critical step in fortifying an organization’s defenses. This includes updating and patching software to close vulnerabilities, enhancing network segmentation to limit the spread of malware, and deploying advanced threat detection and response tools. Organizations should also review and strengthen their access controls, ensuring that only authorized personnel have access to sensitive data and systems. Regular security audits and penetration testing can help identify and address any remaining weaknesses. By continuously improving security measures, businesses can create a more robust cybersecurity posture that mitigates the risk of future attacks and minimizes potential damage.
Training and Awareness Programs
VuduLearn educates employees on cybersecurity best practices is essential for maintaining a strong defense against ransomware and other cyber threats. Regular training sessions should cover topics such as recognizing phishing emails, using strong passwords, and following proper data handling procedures. Interactive and engaging training programs can help employees retain information and apply it in their daily work. Additionally, fostering a culture of security awareness encourages employees to report suspicious activities and follow security protocols diligently. By keeping cybersecurity at the forefront of organizational priorities and ensuring that employees are well-informed, businesses can significantly reduce their vulnerability to cyber attacks and enhance their overall security posture.
US Cyber and Law Enforcement
Government Agencies and Law Enforcement
FBI Cyber Crime Division
- Website: https://www.fbi.gov/investigate/cyber
- Contact: Local FBI field office or submit a tip online.
CISA (Cybersecurity and Infrastructure Security Agency)
- Website: https://www.cisa.gov
- Contact: Email: central@cisa.gov
FTC (Federal Trade Commission)
Contact: Report fraud online or call 1-877-FTC-HELP.
Website: https://www.ftc.gov/tips-advice/business-center/small-businesses
Cybersecurity Organizations
ISACs (Information Sharing and Analysis Centers)
- Website: National Council of ISACs
- Contact: Check individual ISAC websites for specific industry contacts.
Contact: Email: info@sans.org
SANS Institute
Website: https://www.sans.org
Legal and Insurance Resources
American Bar Association (ABA) – Cybersecurity Legal Task Force
Contact: Service@americanbar.org
Website: https://www.americanbar.org/groups/leadership/office_of_the_president/cybersecurity



